Many data sources, like public APIs, are simple to set up without requiring any IT work. However, for your production databases, like Postgres or MongoDB, it’s advised to not keep your database connections publicly available. Password-protecting your databases is a good start for protecting you against unauthorized access, but we recommend you also block connections from unrecognized sources on the network level using a firewall or AWS security groups.
IP Whitelisting
All of Panoply's data sources always use the same range of IP addresses to access your database. In order to still allow Panoply to access your database, you can whitelist the following range of IP addresses in your firewall/network configuration:
52.86.255.240-52.86.255.255, or in CIDR notation use:52.86.255.240/28104.196.134.47, or in CIDR notation use:104.196.134.47/32
AWS Security Groups
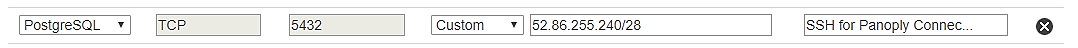
To allow Panoply to access your database instance in AWS:
- Create a Security Group with an Inbound rule.
- Specify your database type.
- Set the protocol type to
TCP. - Set the port to the appropriate port number for your connection.
- Set the Custom range to the CIDR value for Panoply:
52.86.255.240/28,52.168.29.167/32and104.196.134.47/32
To learn more about AWS Security Groups, see Amazon EC2 security groups for Linux instances.
For PostgreSQL, the configuration would look like this: